Using Burpsuite
July 9th, 2019
Reminder: This is for education purposes only, it is not meant for any criminal act or illegal activity.
The tool Burpsuite is very powerful. It can intercept the web traffic, alter the header request, and send altered request. Other services it provides are providing are crawling websites with a spider, bruteforce attack, and many others. For this tutorial, we will intercept our computer’s request and alter the request a bit. Burpsuite is already installed in Kali Linux so you do not need to download it.
Open Burpsuite to start using it. The tool will show the tool starting. 
When the Burpsuite starts, it will show this form window.
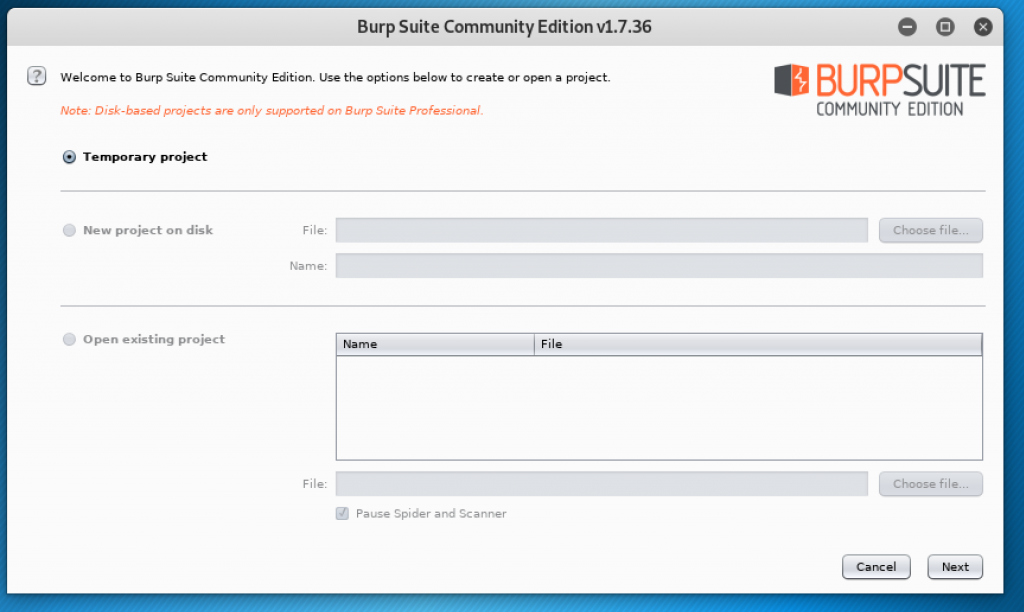
Click on Next. Then the window will show another form asking for the configuration.
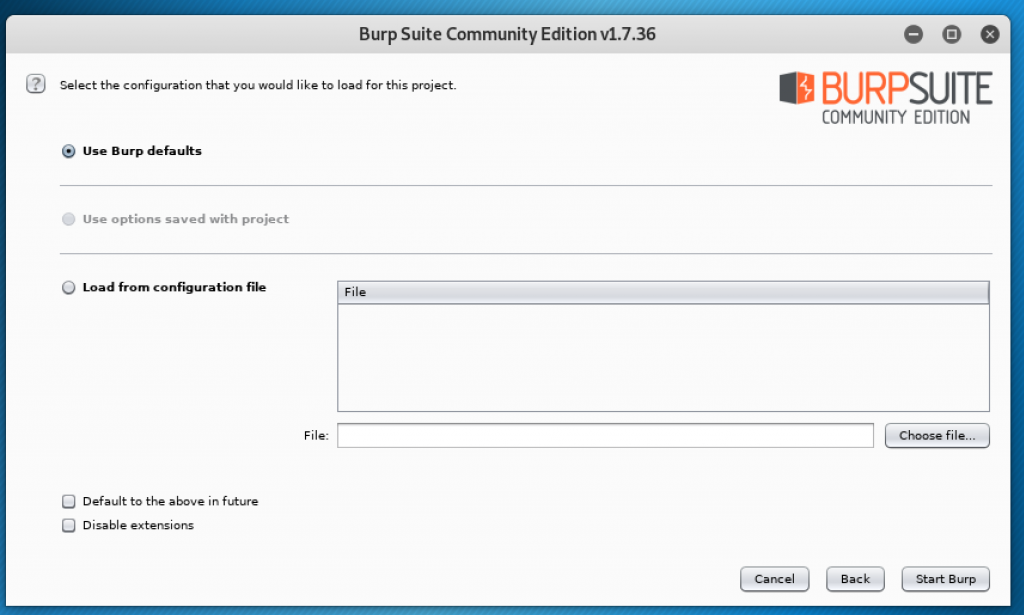
It will choose “Use Burp defaults” by default and then you can begin by clicking on Start Burp. After that, we need to configure the browser so that the Burpsuite can intercept our computer’s requests. Go to your browser and open the preferences or settings.
Go to the Network section and click on the Settings. Click on manual proxy and type 127.0.0.1 (localhost) into the empty field and type 8080 for the port number.
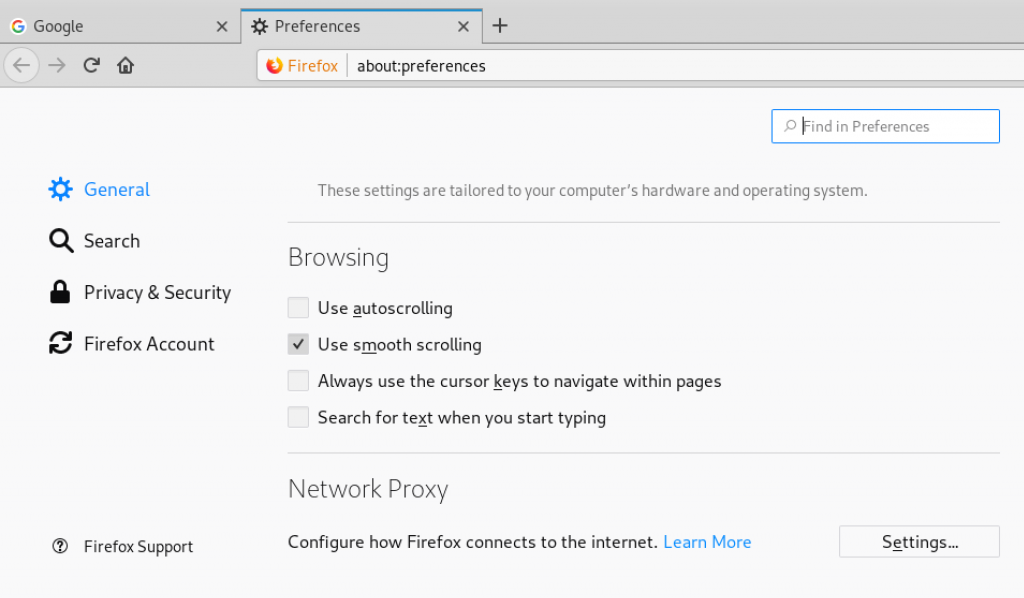
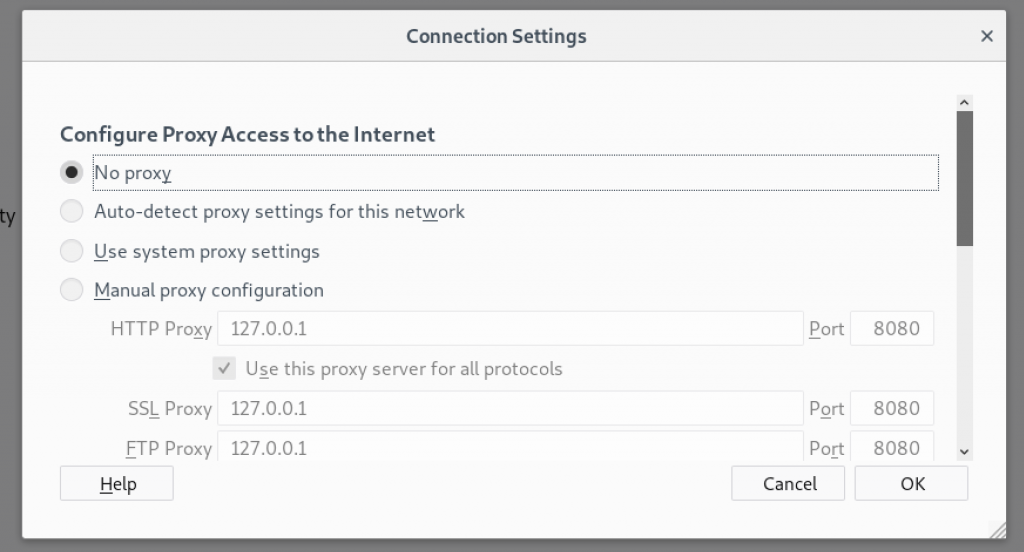
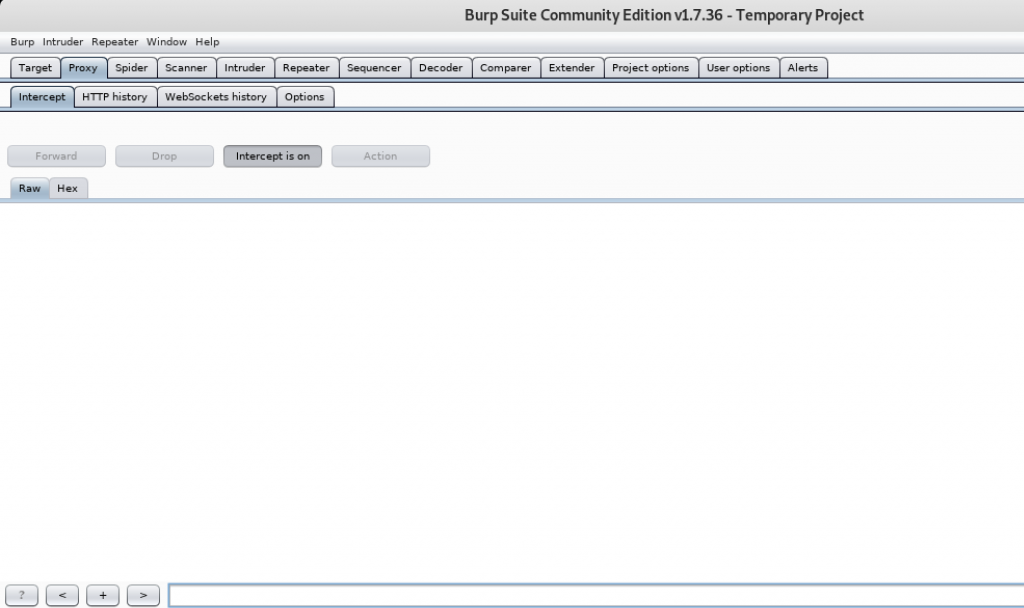
Remember to save the changes and go to Burpsuite to begin the intercept. Open the Proxy tab and make sure intercept is on.
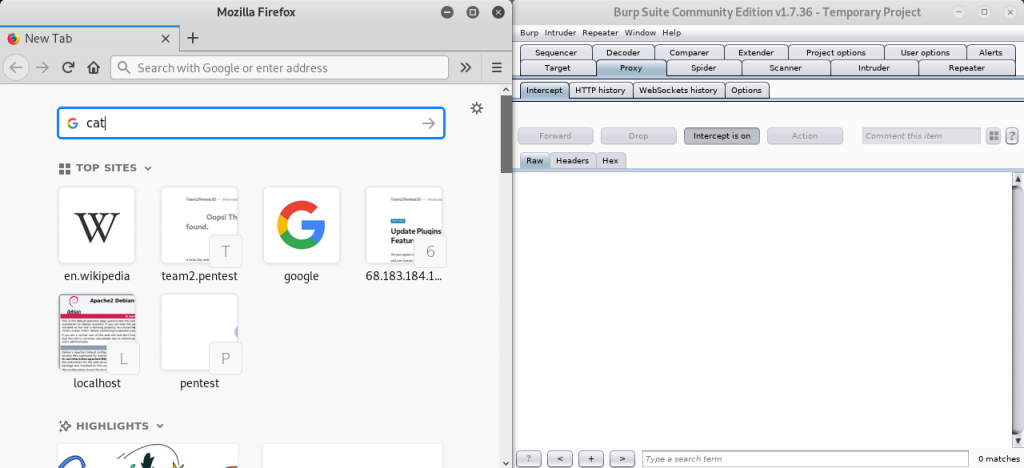
Return back to the browser and search in search engine for anything or open any links to website. I searched for cat.
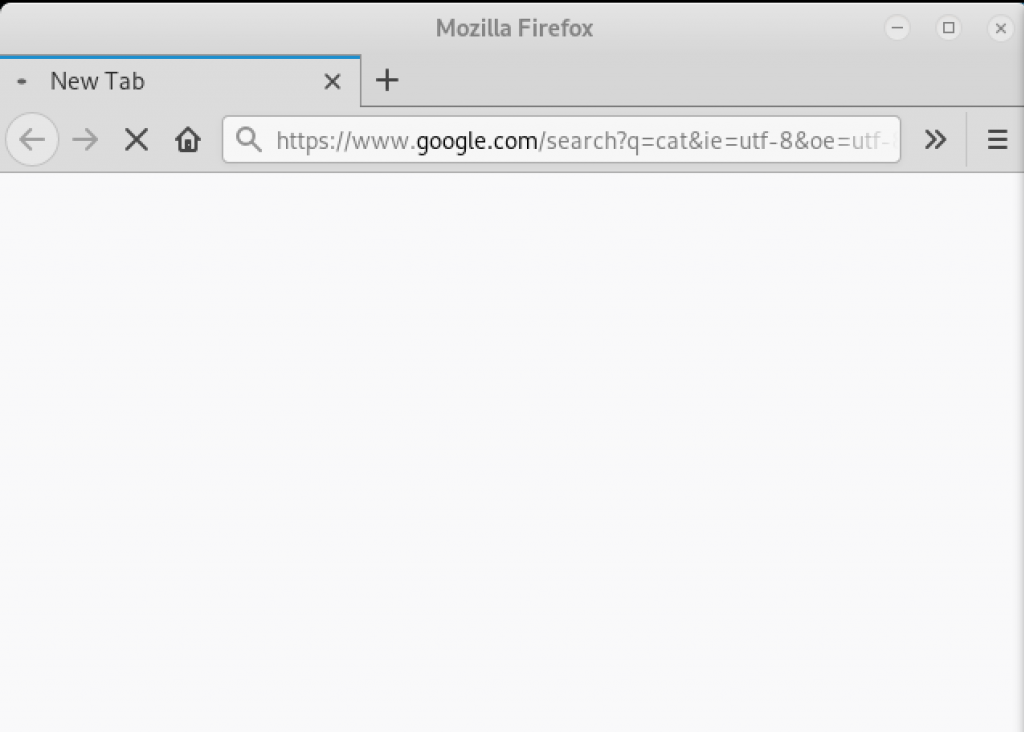
If the page doesn’t load, then the request is intercepted successfully.
Check Burpsuite for the information of the request sent to search for cat.
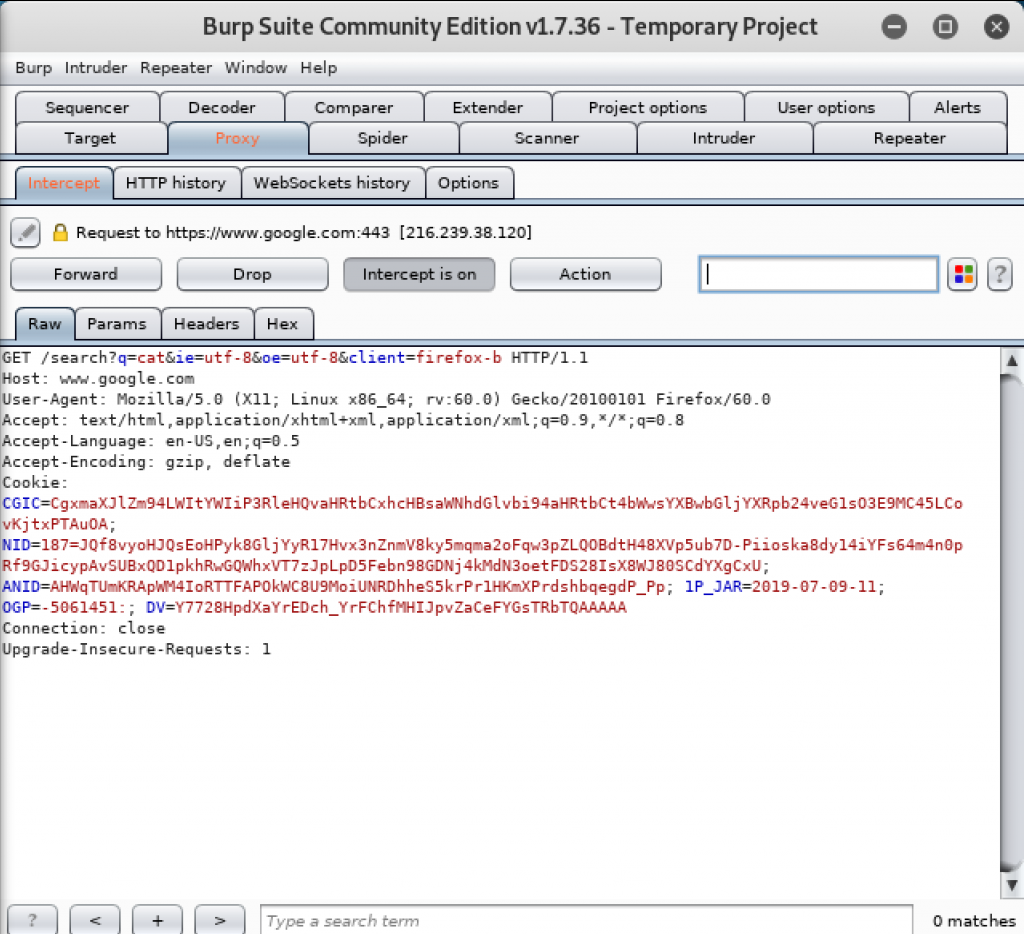
Since the request is being held in Burpsuite, the page will not load until the request is passed to the destination server to be processed. Click on Forward to send the request. The website will load.
If you cannot use Burpsuite because the response returned is SSL Error on the browser, try to change the SSL certificate in the browser and the Burpsuite.
This time I send the request to search for cat again but the request is altered when intercepted before sending it. I changed cat into dog and then forwarded it.
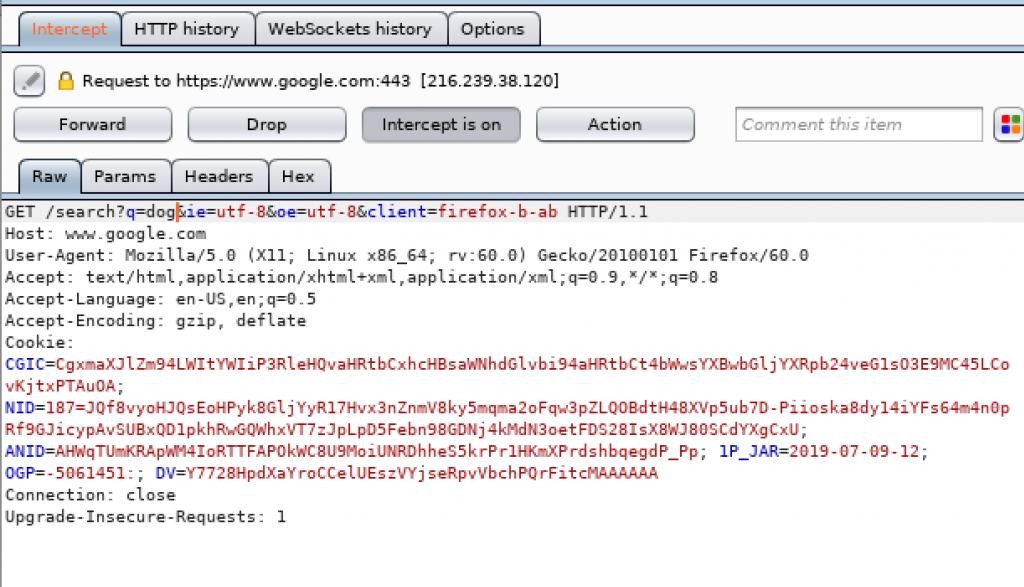
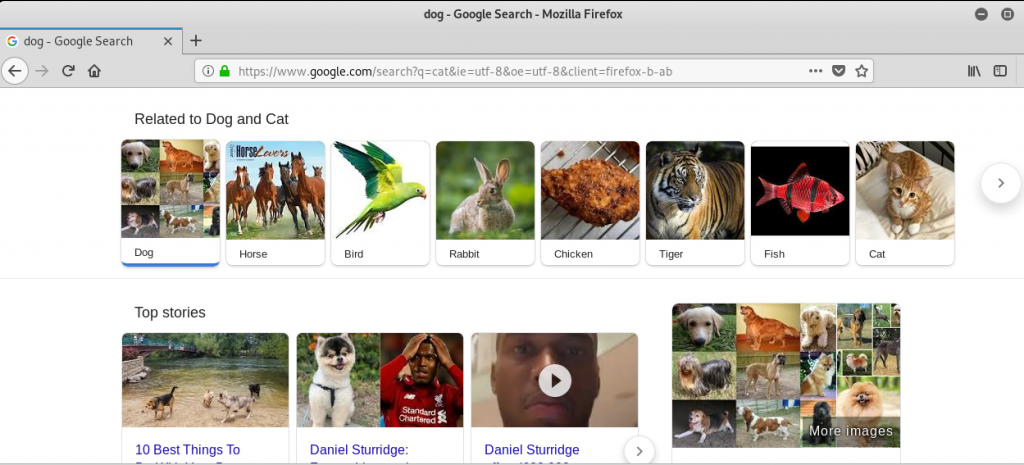
We can also see the history of our intercepted requests by going to the Websocket History tab. Since I intercepted a lot of requests, I have to sort the history based on URL to find the request where I searched for cat.
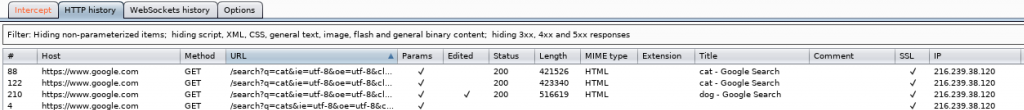
The history intercepted shows the host, the method of the header, the URL, whether the request was edited or modified, the status code of the response, and the title of the page when we searched for cat.
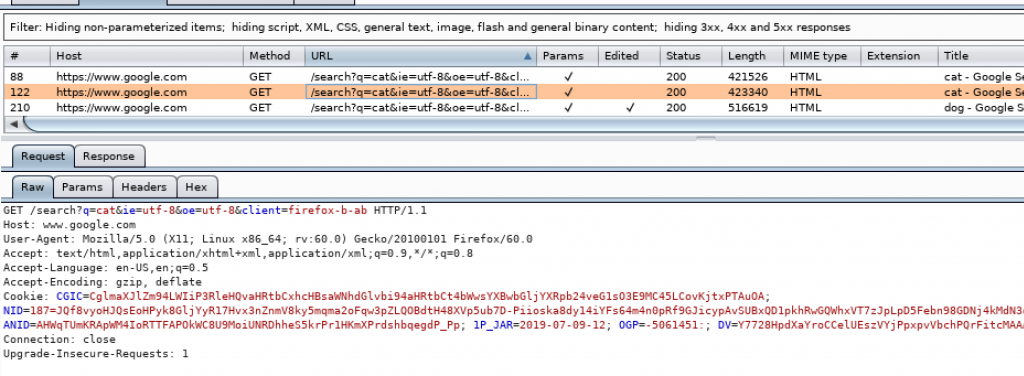
There are the request and the response tab. We can see our request and what the server sent to us as the response. For the request which I edited, it shows the Edited Request tab.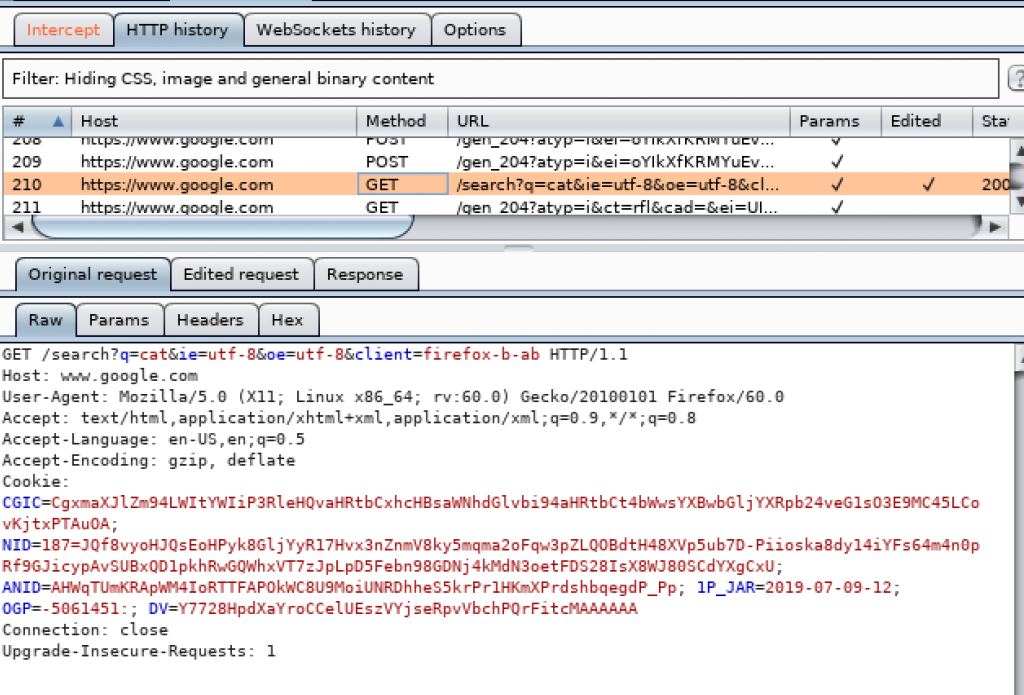
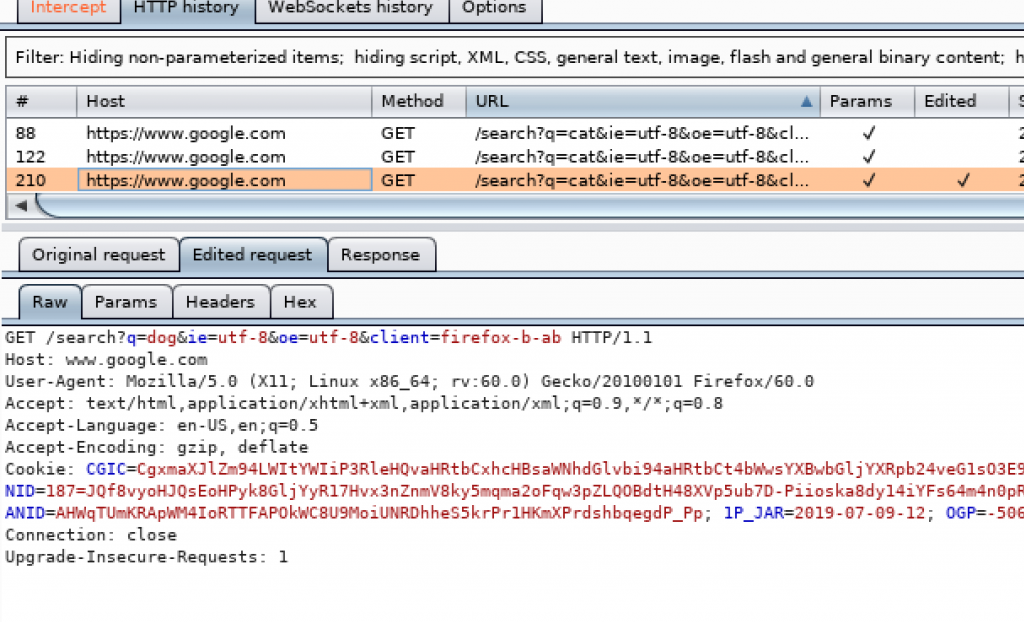
That is one simple way to use Burpsuite.