GEMASTIK 11 Write Up for Kepo Challenge
June 29th, 2019
Reminder: This is for educational purposes only, it is not for criminal act or illegal activities.
My friends and I, a group of three, registered for the national competition for the Cybersecurity section with CTF format which means we need to obtain a piece of data known as “flag” in order to validate the challenge and earn points. We got one case or challenge named “Kepo” which means busybody. The case story tells about someone tried sniffing the packets of his friend’s computer in order to get password for logging in a website, however he got nothing. We had to find the password stored and use it to validate the challenge and get the flag.
First, we downloaded a file named kepo.pcapng and opened it using Wireshark.
We followed the TCP stream and looked at different streams to find any clues.
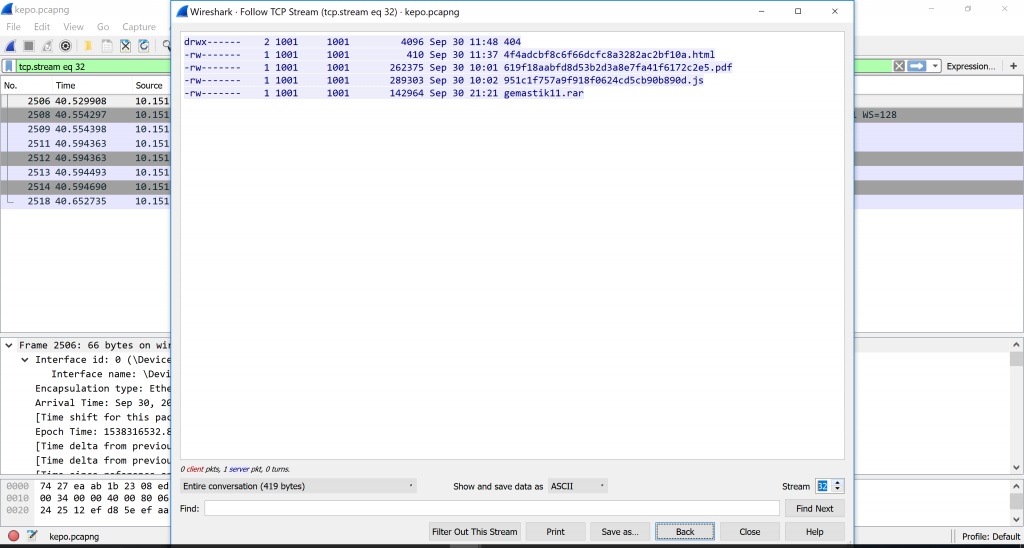
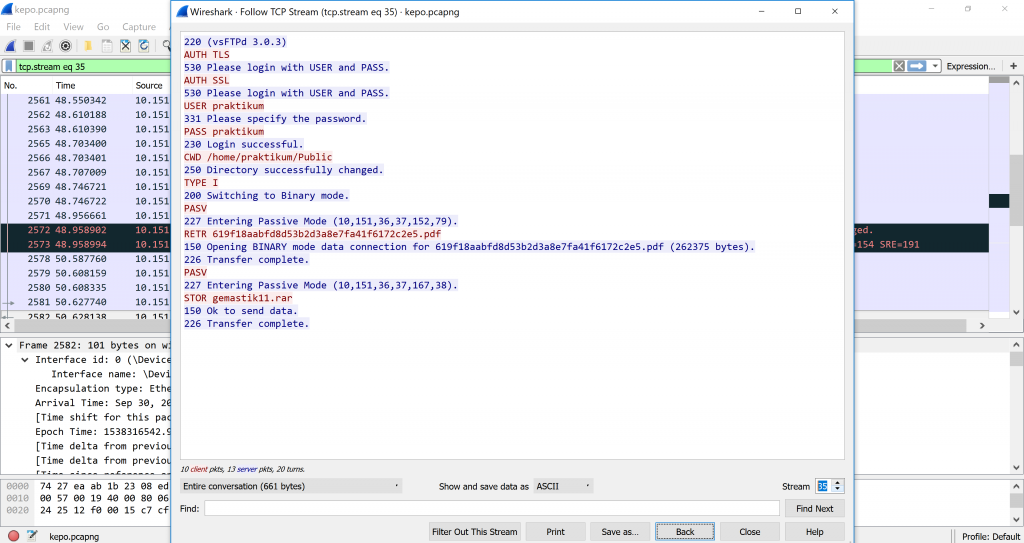
We knew we found the correct clue and the that clue was a compressed folder named gemastik11.rar. Apparently the target makes a STOR request which means he sent data to the server for it to be read and stored in a new file created by the server or replacing a file with the same name. The code 150 means the server accepts the request and code 226 means the storing is complete without any interruptions.
We looked at the next streams and found the stream 37 begins with Rar! and gemastik11.sql in the middle of the second line. It is gemastik11.rar packets.
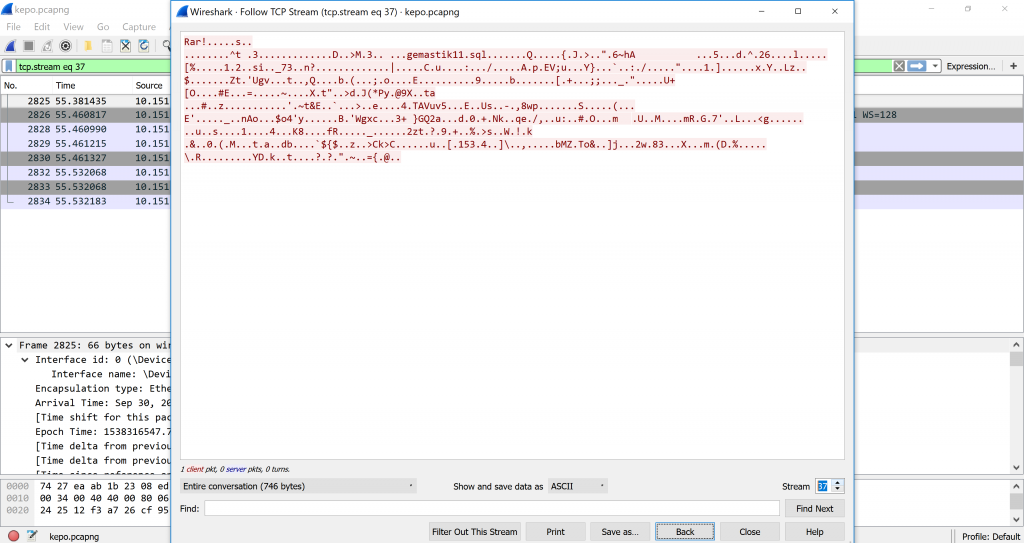 We are beginning to extract the data. First change the dropdown next to the “Show and save data as” from ASCII into Raw.
We are beginning to extract the data. First change the dropdown next to the “Show and save data as” from ASCII into Raw.
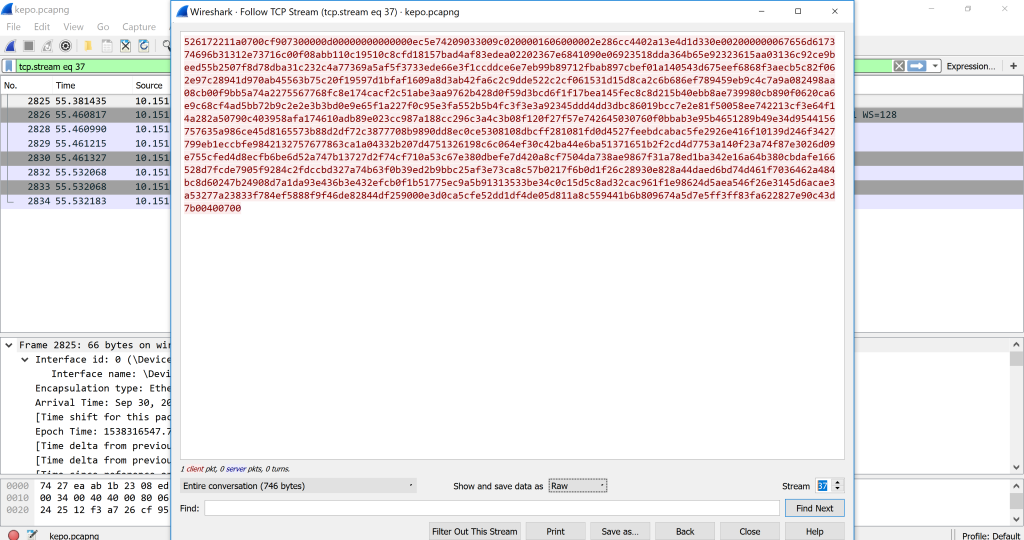
Then we save it as a file named gemastik11.rar.
We opened the folder and found gemastik11.sql.
We opened it and found database information.
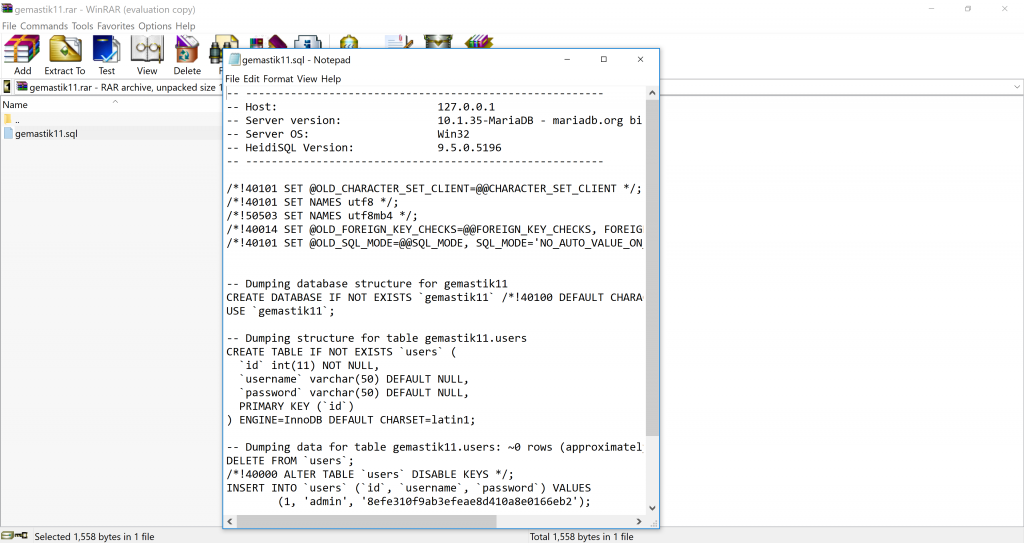
The table containing users has information of the users and the password. We highlighted the information in blue. 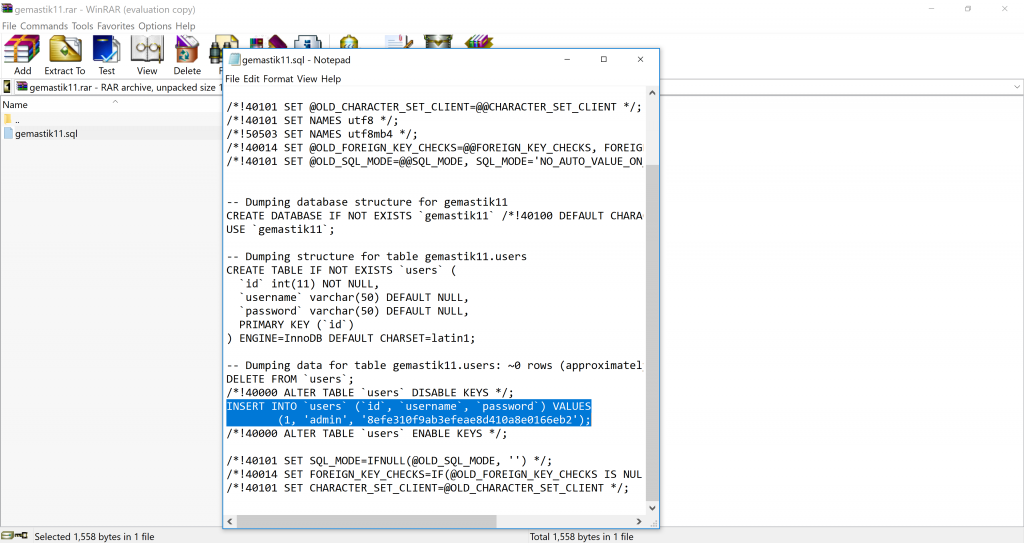
The username admin and the hashed password 8efe310f9ab3efeae8d410a8e0166eb2. The password has 32 characters, we guessed it might be in the form of MD5 hash. So we went to the online hash cracking tool called HashKiller. The link to this online tool is hashkiller.co.uk.
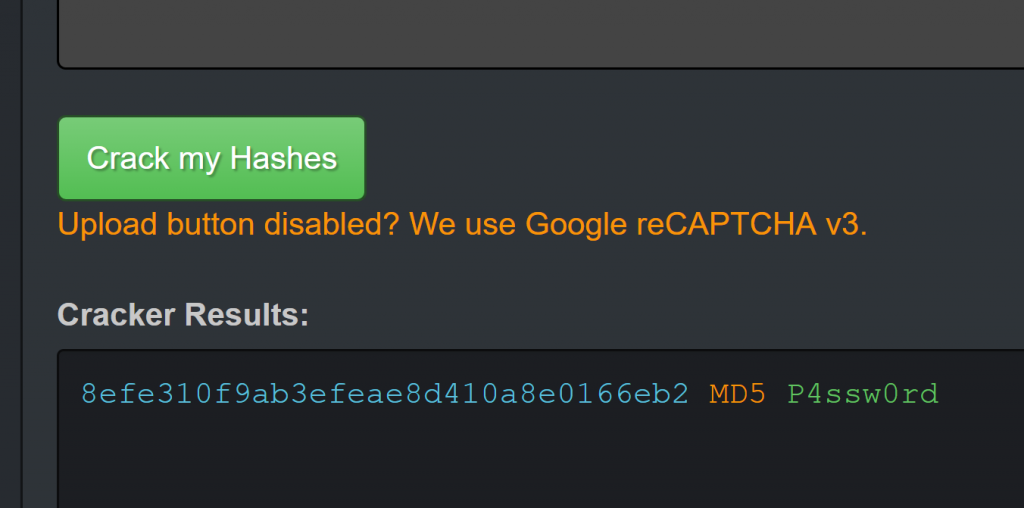
We cracked it and found the password is P4ssw0rd.
We were given the IP address of the machine and the port to connect to. For example, the IP address is 168.192.164.34 and the port is 1234 (We cannot remember the exact numbers so these are fake numbers). We were not given the path to the login page so we guessed with the most common one such as login.php. In the search bar we input 168.192.164.34:1234/login.php and was able to connect and see the login page. We entered the username admin and the password P4ssw0rd and obtained the flag showed on the page in the form GEMASTIK{ }.
I cannot show the screen capture as I had not taken the screen capture of it during the competition.
References:
Bernstein, D.J. (n.d). The STOR, APPE, STOU, ALLO, MKD, RMD, DELE, RNFR, and RNTO verbs.
Retrieved June 28, 2019 from: https://cr.yp.to/ftp/stor.html
Leave a Reply